Every encrypted connection today uses quantum-vulnerable algorithms. Your sensitive data is at risk. QConnect protects data in motion with quantum-safe cryptography.
All communications today use classical encryption standards. AI-powered HNDL (harvest now, decrypt later) attack operations, and quantum computer-powered attacks could expose your communications today. QConnect offers flexible quantum-safe solutions for every environment.

Vulnerable communications
HNDL attack operations are actively exfiltrating and storing communications that are using classical encryption. These communications will be decrypted and exploited. Making your connectivity infrastructure secure reduces risk and financial exposure and maintains customer and partner trust.

Build competitive advantage through trust
Secure connectivity maintains business continuity but privacy protection also creates business opportunities and competitive advantage. Building trust and loyalty is essential today and QConnect gives you confidence to accelerate partnerships through privacy assurance.

Federal mandates require quantum-safe migration
The United States National Institute of Standards and Technology (NIST) identifies post-quantum cryptography (PQC) as critical. CNSA 2.0 compliance requires quantum-safe algorithms for sensitive communications.
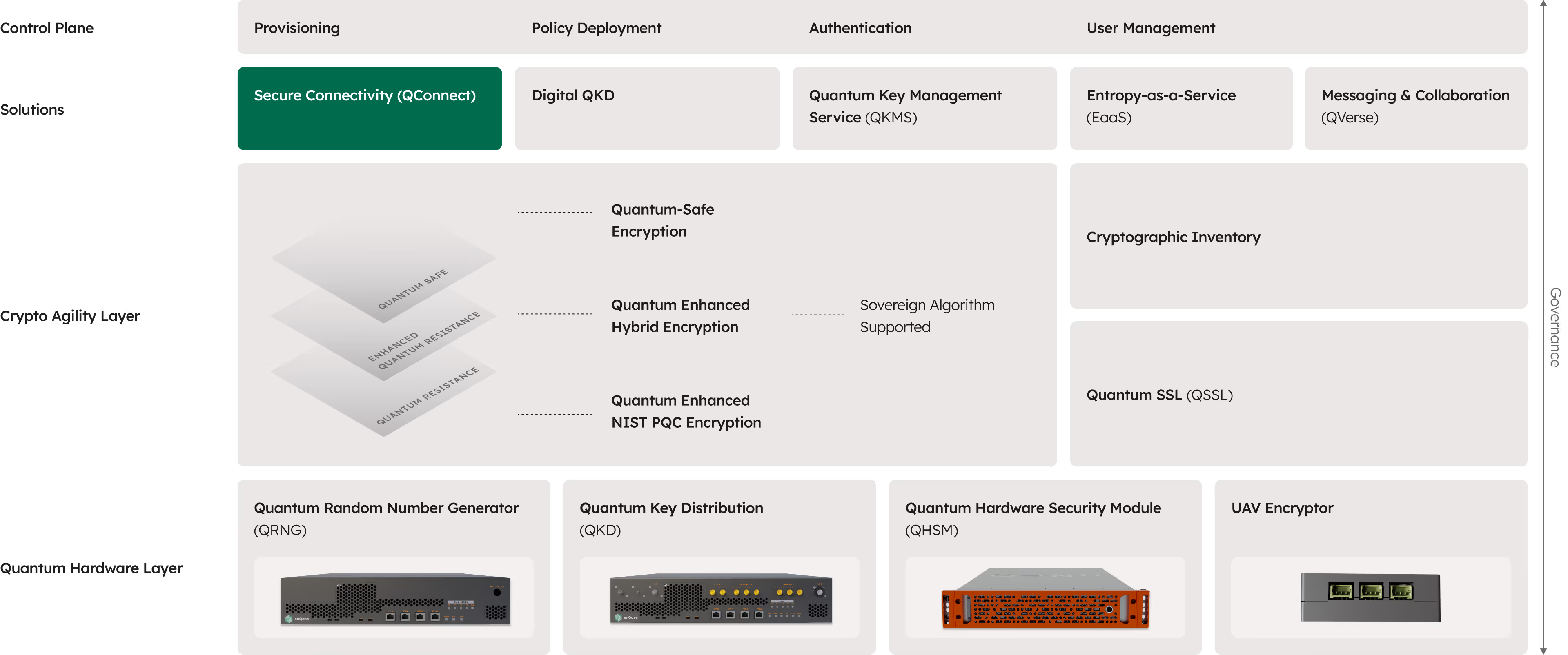
Secure every connection with quantum-safe encryption. QConnect protects data in motion, transitions seamlessly to new standards, and centralizes control across your infrastructure.

Quantum-safe cryptography for data in motion
QConnect is CNSA 2.0 compliant. It uses quantum-safe algorithms strengthened with QRNG (Quantum Random Number Generator) to encrypt and protect every packet of data transmitted.

Crypto-agility
QConnect meets evolving NIST PQC standards cost-effectively. It transitions your systems from classical standards to PQC algorithms without disruption.

Quantum-safe library
Secure your connections with QSSL, the quantum-safe building block of QConnect. QSSL transforms popular open-source libraries you already use into quantum-safe solutions.

Centralized visibility and control
Control your entire quantum-safe infrastructure from one dashboard. Provision servers and users, monitor connections and throughput in real time, identify issues before they impact operations, and distribute certificates through quantum-safe channels.
10 miles, 100 miles, 1500 miles. Learn how enQase can protect all of your sensitive communications.
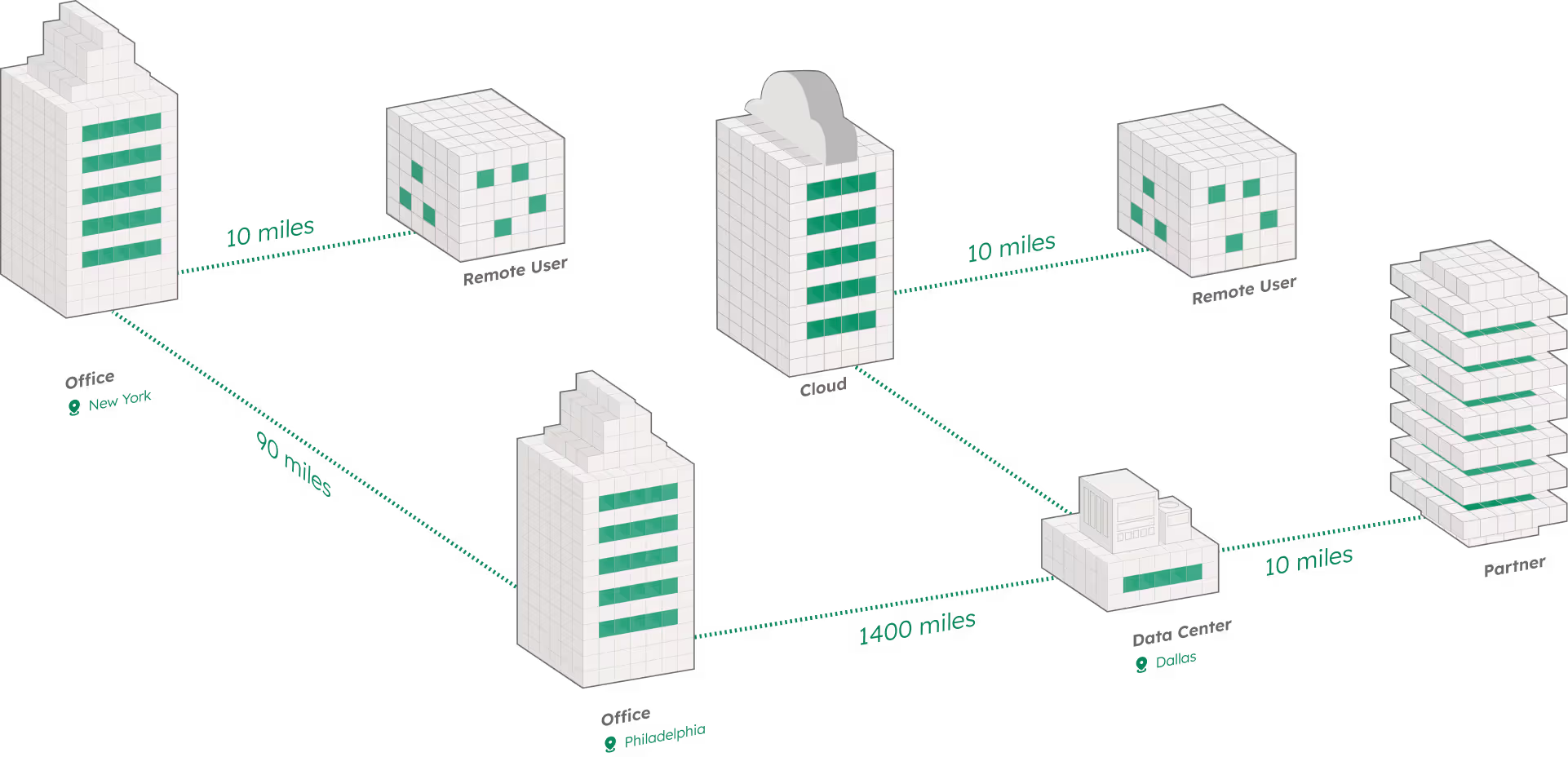
QConnect is your quantum-safe alternative to VPN (Virtual Private Network).
QConnect Secure Connectivity is delivered through the enQase Platform which abstracts hardware and software for seamless integration. Only the enQase Platform gives you the flexibility to choose and vary your level and types of encryption to meet current and future needs.