Traditional random number generators create predictable patterns. enQase's Quantum Random Number Generator (QRNG) uses quantum physics to create true randomness. Your encryption keys become mathematically unpredictable.
Stop using deterministic algorithms. Start with quantum-grade entropy.
The pseudo random number generators (PRNGs) in use today use mathematical algorithms. True random number generators (TRNGs) use hardware noise. Both create patterns. Both can be reproduced. Adversaries exploit these patterns to break your encryption.

Pseudorandom Number Generators (PRNGs)
Software algorithms transform seed values into number sequences. The same seed always produces the same output. Adversaries who can predict your seed can predict every future key your system generates.

True Random Number Generators (TRNGs)
Hardware noise sources produce randomness from thermal fluctuations or electrical variations. Environmental conditions degrade entropy quality over time. High-demand periods may force your TRNG systems to reuse weak random values.

Weak randomness means weak security
Every encrypted file, secure connection, and digital signature starts with a random number. Predictable randomness creates vulnerable encryption keys across your entire infrastructure. One weak key compromises your entire cryptographic chain.

Failed compliance audits for FIPS 140-3 and CNSA requirements
Regulatory standards demand provable randomness quality. PRNGs and TRNGs fail rigorous statistical testing required for federal compliance. Your enterprise faces audit failures, delayed certifications, and restricted access to government contracts.
Quantum physics is fundamentally random. No algorithm. No pattern. No predictability. enQase's QRNG captures this quantum randomness to generate keys that pass the most rigorous security standards.

NIST certified quantum entropy
Pass the highest security standards. Our QRNG meets NIST ESV certification (SP 800-90B), necessary for FIPS 140-3 compliance.

Continuous validation
Built-in test suites verify randomness quality in real time, continuously. Only validated random numbers reach your applications.

Zero pattern generation
Quantum mechanics guarantees true randomness. Each bit is independent and unpredictable. Adversaries cannot find patterns to exploit.

100 Mbps true randomness
Generate cryptographic keys at enterprise scale. Support thousands of secure connections simultaneously without compromising on entropy quality.

Multiple deployment options
Choose the form factor that fits your environment. The enQase Platform enables you to deploy QRNG in data centers, edge locations, IoT devices, or air-gapped systems.
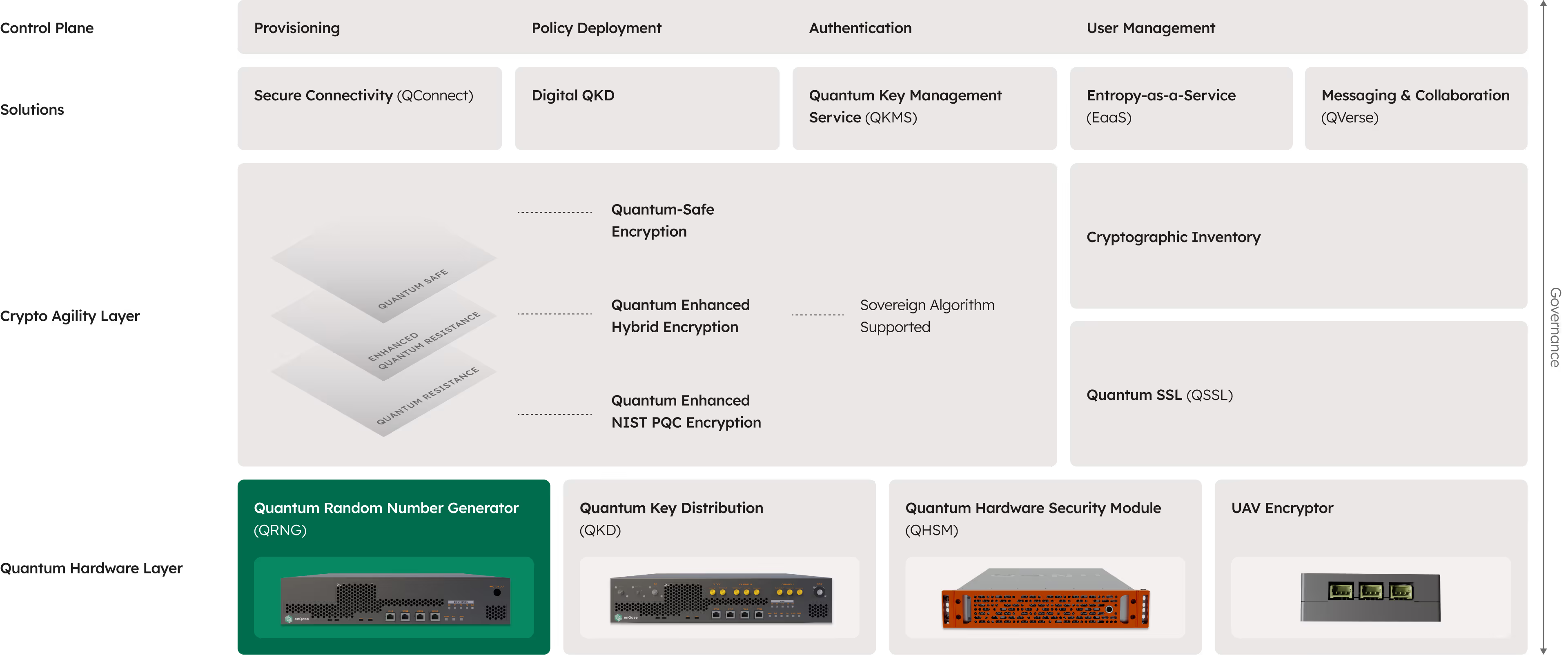
Match your security needs with the right deployment model. From data centers to edge devices, enQase delivers quantum-grade randomness at any scale.
QRNG Enterprise (2U)
Perfect for data centers through HTTPS, PQC TCP, or Open API interface
QRNG Compact (1U)
Perfect for data centers through HTTPS, PQC TCP, or Open API interface in half the rack space
QRNG Lite (Handheld)
Perfect for enterprises, IoT devices and laptops through HTTPS, PQC TCP interface
QRNG Module (Chip)
Perfect for IoT devices and drones through UART interface
QRNG USB
Perfect for laptops through USB 3.0
enQase's QRNG delivers quantum entropy that traditional random number generators cannot match. See the difference for yourself.
QRNG powers our platform delivering quantum-safe solutions for enterprise. Only the enQase Platform gives you the flexibility to vary your level and types of encryption to meet current and future needs. Seamless, painless cryptographic agility.