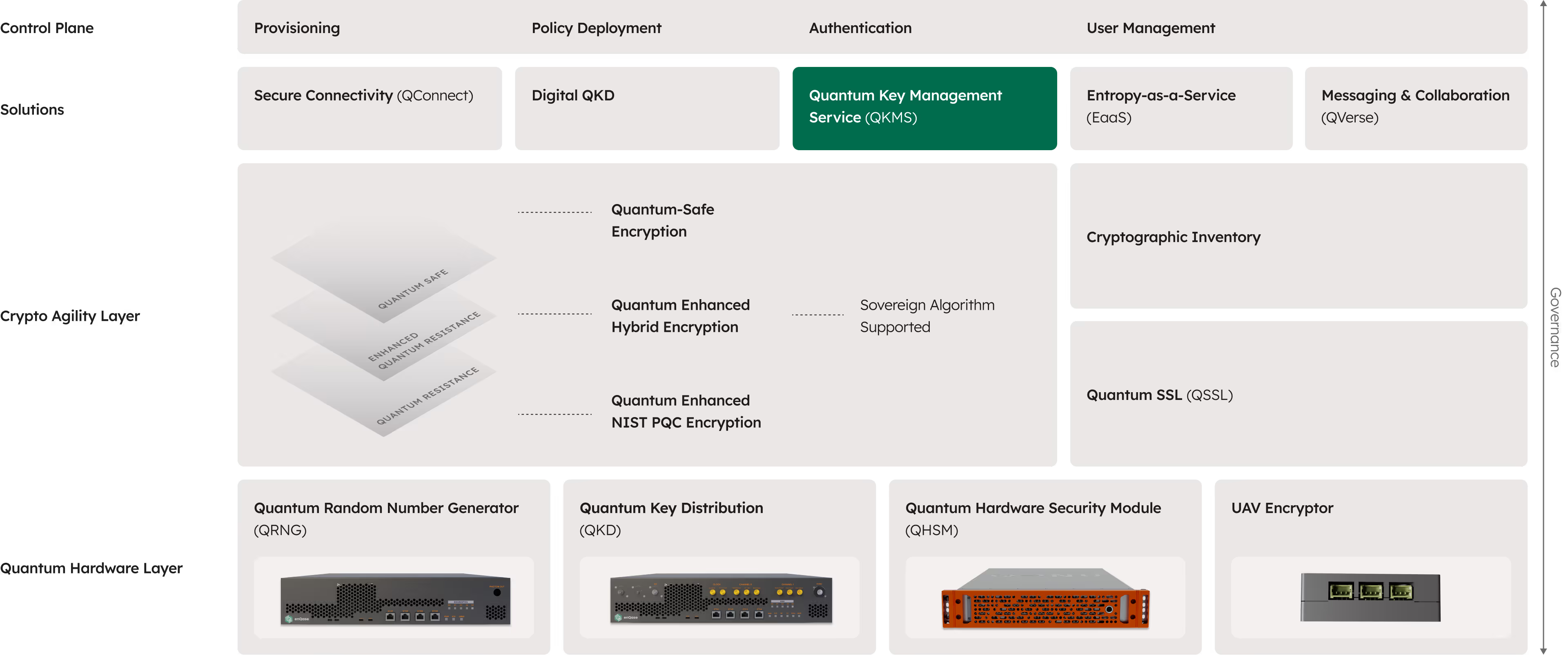
Your encryption keys protect your sensitive data. QVault key management manages the complete lifecycle from creation through distribution, rotation, and revocation. It enhances protection with quantum entropy sources like Quantum Random Number Generator (QRNG).
QVault is a single unified solution for classical and quantum encryption key management.

Crypto agile foundation
QVault meets evolving NIST PQC standards cost effectively. It transitions your systems from classical standards to PQC algorithms without disruption.

Centralized key policy management
Create, manage and apply policies to encryption keys enabling fine grain access control. QVault provides audit logs that track every key operation for compliant reporting and monitoring.

Enhanced NIST Post Quantum Cryptography (PQC)
enQase QVault creates a NIST PQC compliant key management solution. These keys protect your sensitive data from both quantum and classical threats.

Powered by Quantum Hardware Security Module (QHSM)
QHSM provides a hardware backed foundation of trust. It securely generates and stores keys in a tamper-resistant environment. QVault Key Management then manages the full lifecycle including distribution, rotation, revocation, and access control.
QVault is a comprehensive key management solution that outperforms all other solutions in one or more ways.
QVault and QHSM are delivered through our platform which abstracts hardware and software for seamless integration. Only the enQase Platform gives you the flexibility to vary your level and types of encryption to meet current and future needs. Seamless, painless cryptographic agility.