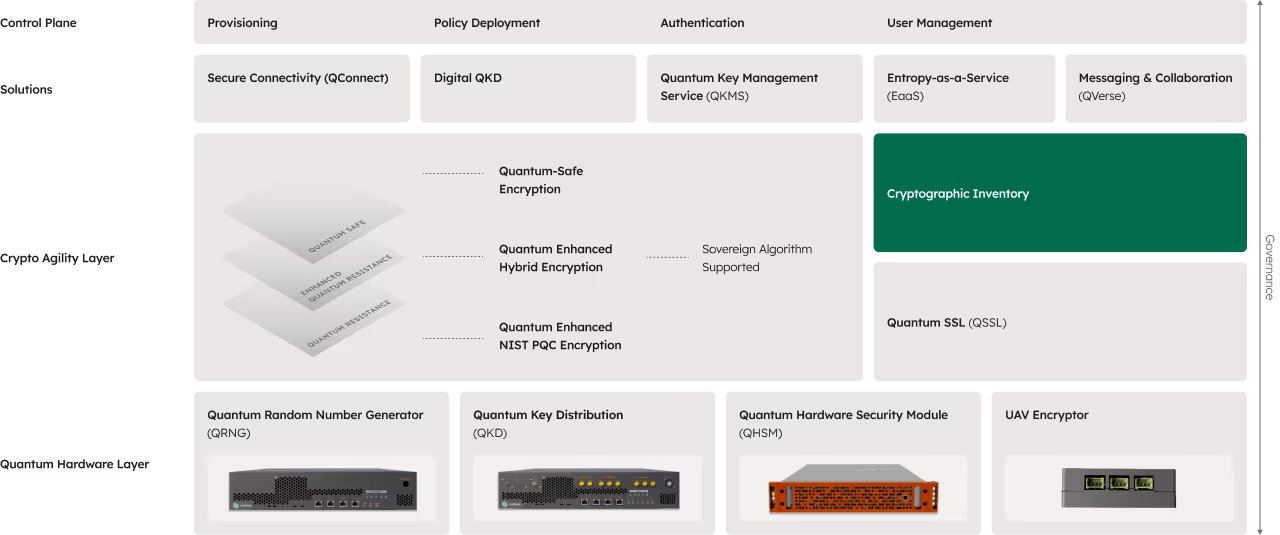
Discovery and inventory of all your cryptographic assets addresses today's vulnerabilities and prepares for quantum threats.
Cryptographic Inventory is your critical first step to reduce risk today and prepare for tomorrow.
Your encryption is everywhere and hidden. You cannot protect what you cannot see. Discover your cryptographic assets today to reduce risk, meet compliance, and defend against quantum threats.

Unknown assets create financial risk
AI-powered attacks, harvest-now decrypt-later (HNDL) operations, and quantum computers threaten classical encryption today. A Cryptographic Inventory quantifies your exposure and prioritizes quantum-vulnerable systems before they're exploited.

Hidden encryption creates blind spots
Keys, certificates, and algorithms are not visible across your systems, cloud services, legacy infrastructure, and third-party dependencies. These blind spots leave you vulnerable to breaches, compliance failures, and service disruptions. A Cryptographic Inventory reveals every cryptographic asset you don’t see today.

Regulators demand cryptographic visibility and governance
The United States National Institute of Standards and Technology (NIST) identifies Cryptographic Inventory as the critical first step for Post Quantum Cryptography (PQC) compliance. Compliance starts with knowing what you have.

Build competitive advantage through trust
Privacy protection creates business opportunities. A Cryptographic Inventory accelerates partnerships with confidence and differentiates you through privacy assurance. Build lasting customer trust and loyalty.
Discover every cryptographic; keys, certificates, and algorithms across your enterprise automatically. Prioritize quantum-vulnerable systems and meet NIST PQC compliance.

Know what you have and what to fix
Your enQase-enhanced Cryptographic Inventory shows what you have, where it lives, and what's quantum-vulnerable. Prioritize fixes, meet compliance requirements, and transition to quantum-safe encryption.

Dynamic asset that evolves with your business
Your enQase Crypto inventory can update automatically with changes across your on-premise, Cloud, etc. environments. Cryptographic discovery automation can eliminate manual processes to track changes over time.
CBOM tools leave critical blind spots. A Cryptographic Bill of Materials (CBOM) lists cryptography built into software at the time of its release. A CBOM will not include what you deploy, configure, or run in production. This gap creates security and compliance risks. Cryptographic Discovery and Inventory reveals operational reality across your entire infrastructure.
Seamless, painless crypto-agility can be attained by starting with an enQase Cryptographic Inventory engagement, and utilizing the enQase Platform.