Software-based quantum key distribution eliminates distance and scalability limitations. Deploy quantum-safe keys across unlimited distances supporting 50+ spokes from single hub. Run on any virtual machine, quantum entropy hardware, or dedicated appliance based on requirements.
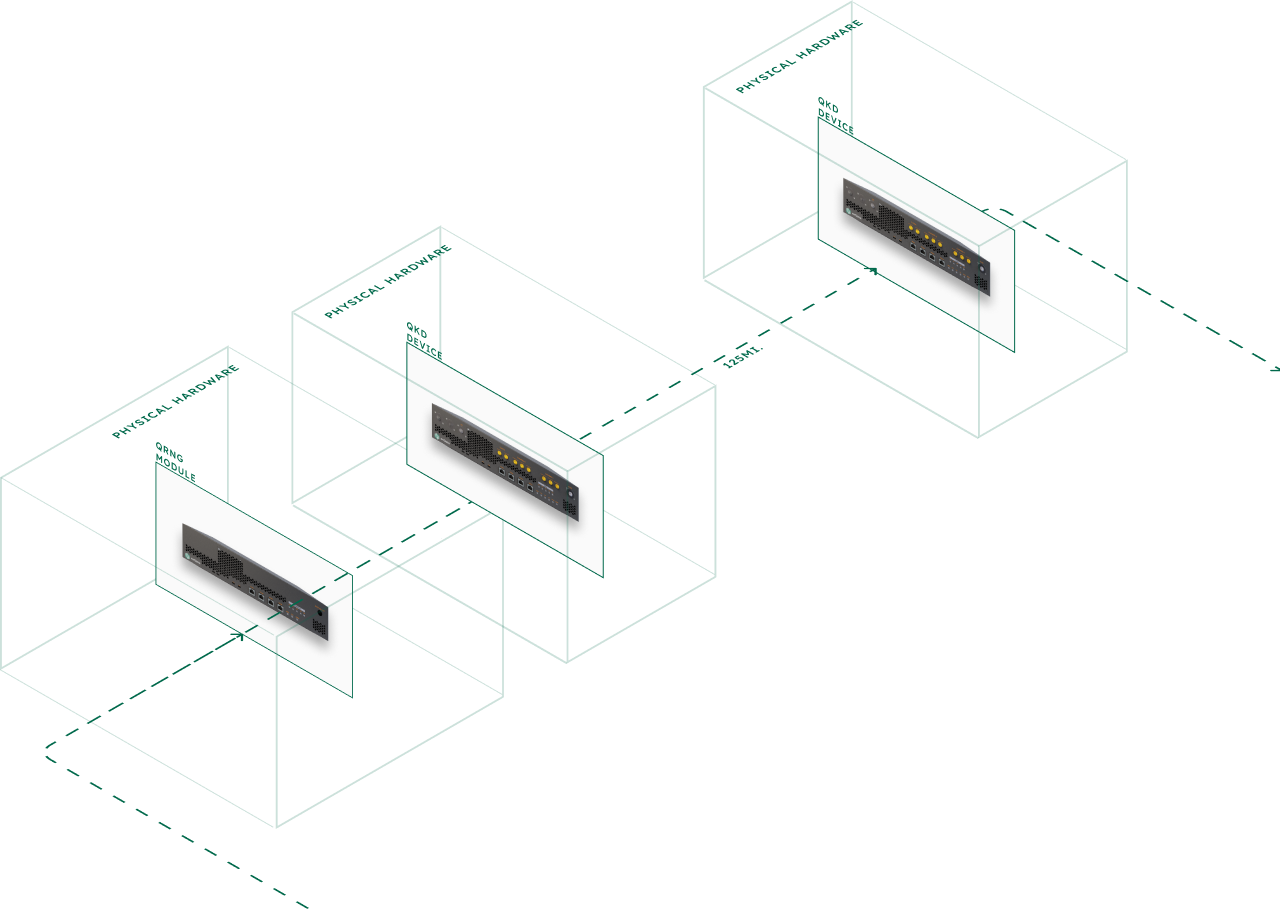
Hardware QKD delivers information-theoretic security for short-distance, high-security scenarios. Many enterprises face different challenges requiring quantum-safe key distribution beyond hardware capabilities. Distance limitations, scalability constraints, and deployment flexibility gaps create security vulnerabilities.
Distance limitations prevent deployment
Hardware QKD operates up to 125 miles over fiber limiting coverage. Your distributed operations span continents requiring quantum-safe keys across unlimited distances.
Scalability constraints limit connectivity
Hardware QKD supports a maximum of 5 spokes in hub configuration, restricting architecture. Your ops may require quantum-safe key distribution across 50+ remote locations.
Hardware deployment creates infrastructure gaps
Physical appliances require data center space, fiber infrastructure, and dedicated hardware investments. Cloud-native and hybrid architectures cannot accommodate hardware QKD deployment requirements.
Distributed architecture demands flexibility
Remote sites, branch offices, and cloud environments require quantum-safe keys immediately. Hardware QKD deployment timelines delay quantum-safe protection for distributed operations.
Digital QKD delivers quantum-safe key distribution through software implementation eliminating distance and scalability limitations. This approach combines Post-Quantum Cryptography (PQC) algorithms with Quantum Random Number Generator (QRNG) entropy. Keys generate using quantum-safe algorithms and distribute over channels protected by post-quantum cryptography.
Complementary to hardware QKD
Hardware QKD uses quantum photon transmission delivering information-theoretic security for short distances. Digital QKD uses PQC algorithms with quantum entropy for software-based distribution. Hardware QKD excels for high-security scenarios within 125 miles and 5 sites. Digital QKD serves distributed operations requiring unlimited distance and massive scalability. Organizations deploy both approaches based on security requirements and architecture.
Software-based architecture advantages
Distance-unlimited deployment supports any separation between endpoints. Scalability expands to 50+ spokes from single hub enabling comprehensive coverage. Flexible execution runs on virtual machines, quantum entropy hardware, or dedicated appliances. Multi-cloud and hybrid architectures gain quantum-safe key distribution without physical constraints.
How it works
Both endpoints run identical key management stacks including generation, migration, and fetching. PQC algorithms combined with quantum entropy create quantum-safe keys at each location. Key management coordinates synchronization and distribution across all connected spokes. Application interface management integrates with existing encryption systems and security infrastructure. Post-quantum cryptography protects all key distribution communications against quantum threats.
Zero-trust requires zero-predictability at source
Zero Trust architecture demands verification at every connection without assumptions about network security. Cryptographic authentication provides the verification mechanism for zero-trust implementation and predictable random numbers undermine the cryptographic foundation that Zero Trust architecture requires.
Production-ready Digital QKD delivers enterprise-grade performance for your distributed operations. Flexible deployment options support virtual machines, quantum entropy hardware, and dedicated appliances. Standards-compliant integration works with your existing key management systems and encryption infrastructure.
Distance-unlimited deployment
Deploy quantum-safe key distribution across your global operations without physical limitations. Point-to-point and point-to-multipoint architectures support operations spanning continents.
Massive scalability
Single hub supports 50+ spoke connections enabling comprehensive coverage across your distributed network. Scale quantum-safe key distribution across your entire enterprise infrastructure.
10KBps key rate per spoke
High-throughput key generation supports your demanding enterprise encryption needs. Sustained key rates enable continuous encryption key rotation across all endpoints.
Flexible execution environment
Run on your virtual machines with quantum entropy integration for cloud deployments. Deploy on quantum entropy hardware or dedicated appliances based on your security requirements.
Software-based standards integration
ETSI GS QKD 014 and Cisco SKIP Protocol support enables integration without hardware dependencies. Virtual machine deployment provides standards-compliant key distribution across your cloud infrastructure.
Post-quantum secured distribution
All key distribution communications protected with NIST-approved cryptography algorithms. Software-based security eliminates specialized fiber infrastructure while maintaining quantum-safe protection.
Different infrastructure architectures require different deployment approaches. Virtual machine, quantum entropy hardware, and dedicated appliance options support cloud, hybrid, and on-premises environments. Choose deployment pattern matching your security requirements and operational infrastructure.
Deploy Digital QKD on virtual machines across public cloud, private cloud, and hybrid environments. Cloud-native deployment eliminates physical infrastructure requirements enabling rapid quantum-safe key distribution. Integration with cloud-based quantum entropy services provides true randomness for key generation. Virtual machine approach scales dynamically supporting growing operations without hardware procurement.
Distribute quantum-safe keys across Amazon Web Services, Microsoft Azure, Google Cloud, and private clouds. Post-quantum secured channels protect key distribution over public internet without dedicated fiber infrastructure. Multi-cloud operations gain consistent quantum-safe key management across all cloud providers. Enable secure workload migration between clouds with quantum-safe key portability.
Connect on-premises data centers with cloud infrastructure using quantum-safe key distribution. Protect hybrid applications and data synchronization with post-quantum cryptography algorithms. Virtual machine deployment supports consistent security architecture across physical and cloud environments. Maintain operational flexibility while achieving comprehensive quantum-safe key coverage.

Deploy Digital QKD on servers equipped with quantum entropy hardware modules for true randomness. Hardware-based entropy eliminates pseudo-random number generator vulnerabilities in key generation. Quantum entropy provides unpredictable keys that adversaries cannot reproduce or predict. Enhanced security meets requirements for financial services and defense operations.
Install quantum entropy appliances in data centers for high-security key generation. Dedicated hardware delivers sustained quantum entropy supporting continuous key rotation requirements. Integration with existing rack infrastructure minimizes deployment complexity and timeline. Quantum entropy validation meets compliance requirements for banking and critical infrastructure sectors.
Hardware quantum entropy delivers high-throughput randomness supporting demanding encryption operations. Continuous quantum randomness enables rapid key generation across all distributed spokes. Sustained performance eliminates entropy starvation creating vulnerabilities in high-volume environments. Mission-critical operations maintain security without performance degradation.

Deploy purpose-built Digital QKD appliances for maximum performance and security. Dedicated hardware eliminates shared resource vulnerabilities present in virtual machine deployments. Tamper-evident physical security protects key generation infrastructure from supply chain attacks. Appliance-based deployment delivers deterministic performance for mission-critical operations.
Financial services, defense, and critical infrastructure operators require dedicated quantum-safe key infrastructure. Purpose-built appliances provide isolated key generation preventing cross-contamination from other workloads. Hardware root-of-trust ensures only verified firmware executes protecting against unauthorized modifications. Real-time monitoring detects any security anomalies before operations are compromised.
Defense contractors and federal agencies require quantum-safe key distribution meeting stringent security mandates. Dedicated appliances satisfy compliance requirements for physically isolated cryptographic operations. Federal Information Processing Standard (FIPS) validation and security certifications demonstrate adherence to standards. Deployment in secure facilities protects classified communications with quantum-safe security.
Global enterprises, financial institutions, and critical infrastructure operators require quantum-safe keys across distributed operations. Each sector faces unique challenges from distance limitations and scalability constraints. Digital QKD delivers software-based quantum-safe key distribution meeting sector-specific requirements.
Protect wire transfers and transactions across continents with quantum-safe key distribution. Digital QKD distributes encryption keys between Americas, Europe, Asia Pacific, and Middle East operations. Unlimited distance capability secures inter-region communications beyond hardware QKD limitations. Real-time key generation supports high-frequency trading platforms requiring sustained encryption key rotation.
Secure international correspondent banking and cross-border payment networks with post-quantum cryptography. Quantum-safe keys protect Society for Worldwide Interbank Financial Telecommunication (SWIFT) messages from harvest attacks. Multi-region key distribution meets regulatory requirements for protecting customer data. Branch-to-headquarters connectivity spans thousands of miles requiring distance-unlimited quantum-safe solution.
Connect trading floors, data centers, and disaster recovery sites across financial networks. Proprietary algorithms and trading strategies require quantum-safe protection against sophisticated adversaries. Low-latency key distribution maintains millisecond-sensitive trading operations without performance degradation. Post-quantum secured channels protect market data and order flow across intercontinental connections.

Distribute quantum-safe keys across headquarters, regional offices, branch locations, and remote sites. Scalability supporting 50+ spokes enables comprehensive coverage beyond hardware QKD limitations. Software-based deployment eliminates fiber infrastructure requirements for connecting distant office locations. Virtual machine execution in branch offices reduces hardware costs and deployment complexity.
Provide quantum-safe encryption keys for remote manufacturing facilities, distribution centers, and field offices. Distance-unlimited capability connects sites regardless of separation or fiber availability. Cloud-based key distribution supports mobile workforce and temporary project sites. Operational flexibility enables rapid deployment without physical infrastructure investments.
Extend quantum-safe key distribution to suppliers, logistics partners, and contracted service providers. Secure business-to-business communications protecting intellectual property and commercial sensitive information. Partner connectivity requires flexible deployment supporting diverse infrastructure and security capabilities. Digital QKD scales across extended supply chain networks without hardware appliance constraints.

Distribute quantum-safe keys between public cloud providers protecting multi-cloud application architectures. Amazon Web Services, Microsoft Azure, and Google Cloud workloads require consistent key management. Post-quantum secured channels protect key distribution over public internet without dedicated connectivity. Cloud-native deployment eliminates data center space and hardware procurement requirements.
Connect on-premises infrastructure with public cloud services using quantum-safe key distribution. Hybrid applications require encryption keys synchronized across physical data centers and cloud environments. Distance-unlimited software approach bridges separation between enterprise facilities and cloud regions. Consistent security architecture maintains protection across diverse deployment models.
Protect distributed applications and microservices spanning multiple cloud providers with quantum-safe encryption. Container orchestration platforms require dynamic key distribution supporting rapid scaling operations. Software-based Digital QKD integrates with Kubernetes and cloud-native security infrastructure. Application Programming Interface (API) driven key fetching supports serverless computing and ephemeral workload architectures.

Distribute quantum-safe keys across energy grids, water systems, and utility infrastructure spanning states. Supervisory Control and Data Acquisition (SCADA) communications require protection from quantum threats. Distance-unlimited capability secures control center to substation connectivity exceeding hardware QKD range. Scalability supports hundreds of remote sites requiring quantum-safe key distribution.
Connect air traffic control centers, railway operations, and maritime port facilities with quantum-safe keys. National transportation infrastructure spans thousands of miles requiring distance-unlimited key distribution. Remote facilities lack fiber infrastructure necessary for hardware QKD deployment. Software-based approach protects transportation command and control from quantum computing threats.
Protect telecommunications network infrastructure with quantum-safe key distribution across nationwide coverage areas. Fifth-generation (5G) core network elements require quantum-safe encryption protecting subscriber communications. Base station backhaul networks span continental distances beyond hardware QKD limitations. Massive scalability supports thousands of cell sites requiring quantum-safe protection.

Hardware QKD and Digital QKD serve different use cases within comprehensive quantum-safe strategy. Hardware QKD delivers information-theoretic security for high-security, short-distance scenarios. Digital QKD provides distance-unlimited, massively scalable key distribution for distributed operations. Organizations deploy both approaches based on security requirements and architecture.
Production deployments validate Digital QKD reliability across enterprise infrastructure. Standards-compliant implementation meets federal requirements and enterprise security mandates. Independent certification demonstrates adherence to quantum-safe cryptography and key management standards.
ETSI GS QKD 014 compliant
European Telecommunications Standards Institute (ETSI) Quantum Key Distribution interface standards compliance enables integration. Standard protocols work with your existing key management systems.
Cisco SKIP Protocol support
Standards-based integration enables Digital QKD deployment across your Cisco infrastructure. Software-based protocol implementation eliminates specialized hardware requirements for quantum-safe key distribution.
NIST post-quantum cryptography
CRYSTALS-Kyber and CRYSTALS-Dilithium implementations meet NIST FIPS 203 and 204 standards. Federal agencies adopt NIST-approved algorithms for quantum resistance.
Production deployment validation
Deployed across financial services, telecommunications, and critical infrastructure protecting distributed operations. Real-world validation demonstrates reliability for mission-critical key distribution.
Digital QKD uses software-based quantum-safe key distribution while hardware QKD uses quantum photon transmission. Hardware QKD provides information-theoretic security limited to 125 miles and 5 spokes. Digital QKD provides computational security using NIST-approved post-quantum algorithms without distance or scalability limitations. Both approaches deliver quantum-safe key distribution serving different use cases.
Software-based distribution over standard network connections eliminates fiber distance constraints present in quantum photon transmission. Post-quantum algorithms protect key distribution communications regardless of separation between endpoints. Hardware QKD requires specialized quantum channel limited by photon loss over distance. Digital QKD uses classical networking infrastructure supporting unlimited distance key distribution.
Virtual machine deployment runs on any hypervisor supporting cloud, hybrid, and on-premises environments. Quantum entropy hardware deployment combines software with true quantum randomness for enhanced security. Dedicated appliance deployment provides purpose-built infrastructure for mission-critical operations. Organizations choose deployment option based on security requirements and operational infrastructure.
Both approaches complement each other within comprehensive quantum-safe key distribution strategy. Deploy hardware QKD for maximum security scenarios within 125 miles requiring information-theoretic protection. Use Digital QKD for distributed operations, multi-cloud architectures, and distances exceeding hardware limitations. Integration through standard key management interfaces enables coordinated deployment across diverse infrastructure.
CRYSTALS-Kyber and CRYSTALS-Dilithium algorithms protect all key distribution communications over classical networks. Post-quantum cryptography resists attacks from both classical and quantum computers. NIST-approved algorithms provide computational security validated through extensive cryptographic analysis. Secured channel eliminates need for specialized quantum fiber infrastructure.
Software-based approach generates and distributes quantum-safe keys using post-quantum algorithms with quantum entropy. Keys generate at endpoints using post-quantum cryptography rather than quantum photon transmission. Post-quantum secured classical channel protects key distribution communications against quantum threats. Software implementation eliminates physical infrastructure requirements enabling flexible deployment across virtual machines and clouds.
Software-based architecture eliminates hardware limitations constraining point-to-multipoint configurations to 5 spokes. Each spoke runs identical key management software coordinated through centralized hub. Network bandwidth and computing resources scale to support massive spoke deployments. Virtual machine execution enables dynamic scaling without physical hardware constraints.
System generates up to 10 kilobits per second per spoke supporting sustained encryption operations. Key rate supports continuous key rotation requirements for high-security applications. Throughput scales across all connected spokes enabling comprehensive distributed key distribution. Performance meets enterprise requirements without specialized high-speed quantum channel hardware.
ETSI GS QKD 014 V1.1.1 compliance enables integration with standards-based key management systems. Cisco SKIP Protocol support ensures compatibility with enterprise networking and security infrastructure. NIST FIPS 203 and 204 post-quantum cryptography standards provide quantum-safe algorithms. Custom interface options support proprietary encryption systems and specialized requirements.
Use hardware QKD for maximum security within 125 miles between data centers requiring information-theoretic protection. Deploy Digital QKD for global operations, multi-cloud architectures, and distributed enterprises exceeding distance limitations. Choose Digital QKD when requiring 50+ sites or rapid deployment without fiber infrastructure. Organizations deploy both approaches serving different security requirements within comprehensive quantum-safe strategy.