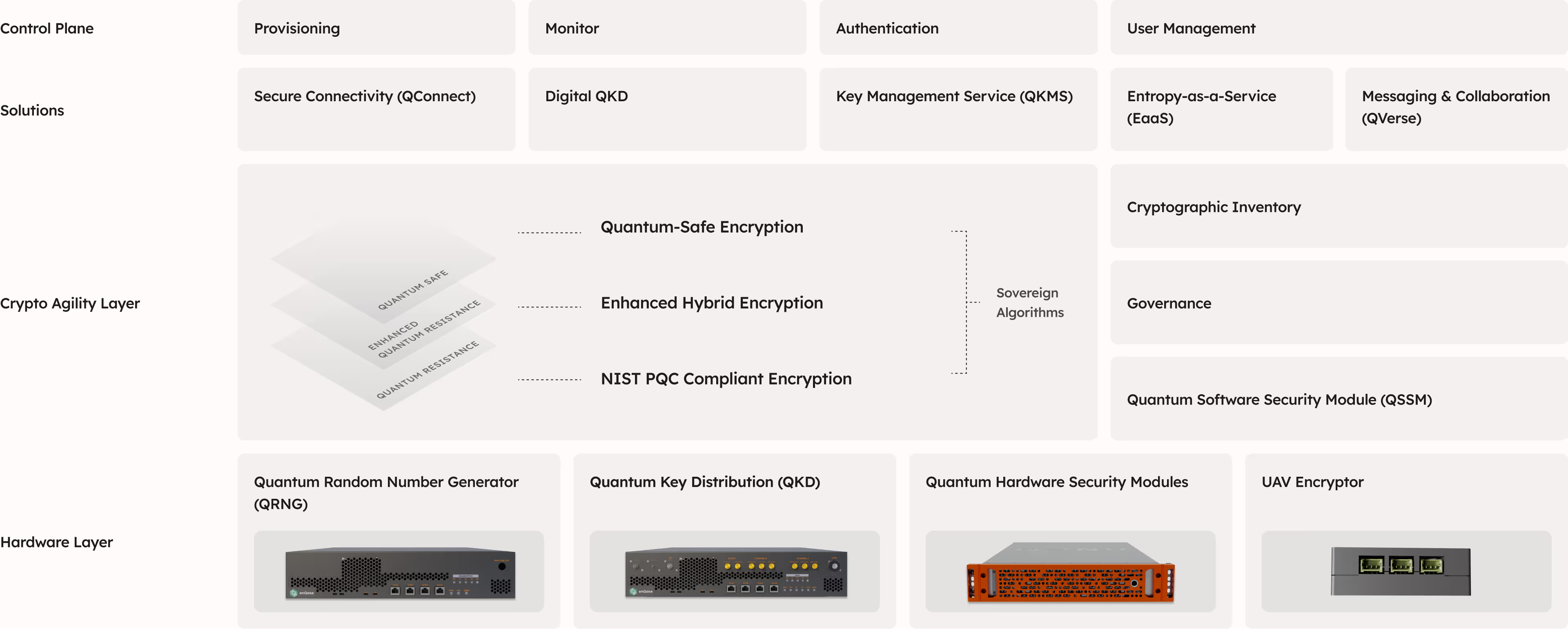
The enQase Platform includes Quantum Random Number Generator (QRNG)-enhanced algorithms to provide more protection, crypto-agility, and meet NIST standards.
Quantum computers will break current encryption standards. Your encrypted sensitive data captured today is at risk of exposure. NIST PQC compliant algorithms enhanced with QRNG protect you from quantum threats.

Harvest Now, Decrypt Later (HNDL) Attacks
HNDL operations are actively storing communication using classical encryption algorithms to be decrypted and exploited. Quantum-safe encryption reduces financial exposure and maintains customer trust.

Build competitive advantage through trust
Data protected by encryption safe from quantum computers creates business opportunities. PQC compliance gives you confidence to accelerate partnerships and differentiates you through privacy assurance. Build lasting customer trust and loyalty.

Federal mandates require quantum-safe migration
The United States National Institute of Standards and Technology (NIST) identifies post-quantum cryptography (PQC) as critical. CNSA 2.0 compliance requires quantum-safe algorithms for sensitive communications.
Post-Quantum Cryptography (PQC) algorithms enhanced with true random numbers from Quantum Random Number Generators (QRNG) protect your sensitive data from quantum computers. Meet federal compliance requirements while strengthening your cryptographic foundation.
Why it matters
NIST PQC algorithms provide quantum resistance. QRNG enhancement eliminates vulnerabilities in random number generation. Your encryption becomes unpredictable to both classical and quantum threats.
Hybrid Enhanced combines NIST PQC algorithms with classical encryption, enhanced by QRNG. Your data stays protected if either algorithm fails. This dual-layer approach provides maximum security during the quantum transition.
Why it matters
Quantum computers arrive on uncertain timelines. Hybrid Enhanced protects you now and later. Your sensitive communications remain secure against today's threats while building quantum resistance for tomorrow.
Deploy Quantum Key Distribution (QKD) and CNSA 2.0 Level 5 algorithms for the highest security standard available. Protect your short distance communications with tamper evident QKD and longer distances with CNSA 2.0.
Why it matters
QKD detects eavesdropping automatically. Your most critical data, intellectual property, and communications gain protection that remains secure regardless of computing advances.
Become PQC compliant with a crypto agile foundation. Only the enQase Platform gives you the flexibility to vary your level and types of encryption to meet current and future needs. Seamless, painless cryptographic agility.